30x Faster Performance and Better Team Visibility
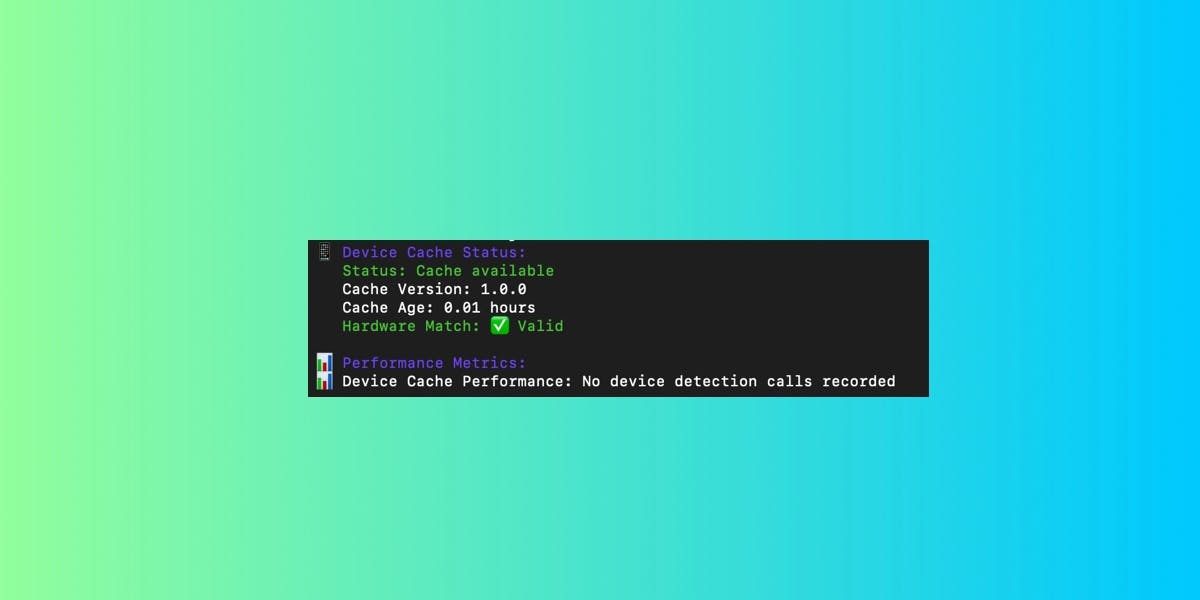
Table of Contents
Menu. Currently selected: 30x Faster Command Execution
We just shipped three major improvements to the DeployStack Gateway that make it faster, more reliable, and give teams better visibility into their MCP usage. Here's what changed and why it matters for your daily workflow.
30x Faster Command Execution
The biggest change: Gateway commands now complete in ~0.1 seconds instead of 3+ seconds.
We implemented an intelligent device caching system that eliminates the expensive device fingerprinting operations that were slowing down every command. Now fingerprinting happens once during login, then gets cached securely for 30 days.
Before:
bash
$ deploystack refresh
⠹ Detecting device information... # 2.8 seconds
⠹ Getting current configuration... # 0.3 seconds
✔ Configuration updated
After:
bash
$ deploystack refresh
⠹ Getting current configuration... # 0.1 seconds
✔ Configuration updated
The cache uses your OS's secure keychain (macOS Keychain, Windows Credential Manager, Linux Secret Service) with AES-256-GCM encryption as a fallback. Cache automatically refreshes every 30 days and validates hardware signatures for security.
Impact: Commands like deploystack refresh and deploystack mcp feel instant. No more waiting around for basic operations.
Automatic Device Activity Tracking
New capability: Teams can now see when devices last accessed DeployStack.
We added background device activity tracking that updates whenever a device calls the platform. This helps teams monitor usage patterns and identify inactive devices for security and license management.
What gets tracked:
- Last activity timestamps for each device
- IP addresses for security auditing
- Usage patterns across team devices
Enterprise benefits:
- Stale device detection - Find devices that haven't been used in months
- Security auditing - Track access patterns and identify anomalies
- License compliance - Monitor active device counts accurately
- Team visibility - See which developers are actively using MCP tools
The tracking happens in the background using hardware fingerprints and won't slow down API responses. All data helps teams maintain better security hygiene and understand their MCP adoption.
Streamlined Configuration Management
Code quality improvement: Eliminated 250+ lines of duplicated configuration change detection code.
We built a reusable ConfigurationChangeService that both the refresh and mcp commands now use. This means consistent behavior, easier maintenance, and better user feedback.
Better user experience during backend operations:
Before:
bash
🤖 MCP Configuration Status
⚠️ No MCP servers configured for this team
[3-second silence with no feedback]
After:
bash
🤖 MCP Configuration Status
⚠️ No MCP servers configured for this team
⠹ Connecting to backend to check for configuration updates...
⠹ Downloading latest configuration from cloud...
⠹ Comparing configurations...
✔ Configuration check completed
The service provides centralized logic for detecting configuration changes, analyzing what changed (added/removed/modified servers), and handling restart prompts when needed.
Technical Architecture
These improvements follow our core design principles:
Performance-first design - Cache expensive operations, provide immediate feedback, optimize for the common case of repeated command usage.
Enterprise-ready security - Use OS-level secure storage, encrypt fallbacks, validate integrity, and provide audit trails for compliance teams.
Developer experience focus - Make commands feel instant, provide clear progress feedback, and eliminate frustrating wait times that break flow state.
Real-World Impact
For a typical developer using DeployStack throughout the day:
- Before: Each deploystack command took 3+ seconds, interrupting workflow
- After: Commands complete instantly, maintaining development flow
- Team visibility: Managers can see which developers are actively using MCP tools
- Maintenance: Easier to identify and clean up unused devices
For enterprise teams managing dozens of developer devices:
- Activity monitoring: Clear visibility into MCP adoption and usage patterns
- Security compliance: Audit trails and stale device detection